I modified the Access Role policy to enable the Captive
Portal if source is HQ-Inside subnet 10.1.1.0/24 going to Any destination using
Any service. For some reason, my log hits are 0 and I did reset by doing a
right-click on a rule > Hit Count > Refresh OR right-click on Hits
column > choose Refresh.
I’ve opened Facebook since it’s HTTPS and Bank of America website to verify both the Inspect and Bypass rule. The green circle with double arrow is the bypass log.
Under Global Properties, you could also
enable/disable Hit Count and how long to store the Hit Count values.
Double-click on the Security Gateway under Network Objects
> Check Point > General Properties > go to HTTPS Inspection.
Follow the steps and in Step 1 click on Create since there’s
no CA server or Public Key Infrastructure (PKI) on the network. Fill up the Distinguished
Name (DN), create a private key password then click OK.
You can view the details on the newly created self-signed
certificate and install it on the SmartConsole PC by following the Certificate
Import Wizard.
You can save and deploy the certificate in order to
distribute to other users via email or pushing it via the Group Policy Object
(GPO) management.
Finally tick on HTTPS Inspection to enable the feature then
click OK. Repeat the same steps for Branch Security Gateway 2.
To view HTTPS Inspection predefined policy, go to URL &
Application Filtering tab > Advanced > HTTPS Inspection > Policy and
enable Log.
Click Save and Install Policy.
I login as a guest user by clicking on the I don’t have a
username and password hyperlink and filled up the info. This is useful if user
is using personal device such as tablet and smartphone.
Click on the terms and conditions hyperlink and it will open
and redirect you to another web browser tab. Tick I have read and agreed to the
terms and conditions and click Next. I was able to browse to Check Point’s
website afterwards.
Go to SmartView Tracker to verify HTTPS Inspection which
depicted by a yellow circle with a looking glass.
I tried to login to a banking site and view the log in
SmartView Tracker.
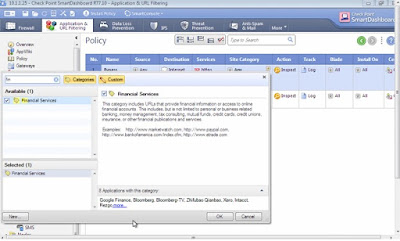
Create a bypass rule under Application & URL Filtering
tab for Banking or Financial sites. Search for Financial Services under the
Site Category column, tick the category, enable Bypass and Log. Click Save and
Install Policy.
I’ve opened Facebook since it’s HTTPS and Bank of America website to verify both the Inspect and Bypass rule. The green circle with double arrow is the bypass log.






























No comments:
Post a Comment